Key Takeaways:
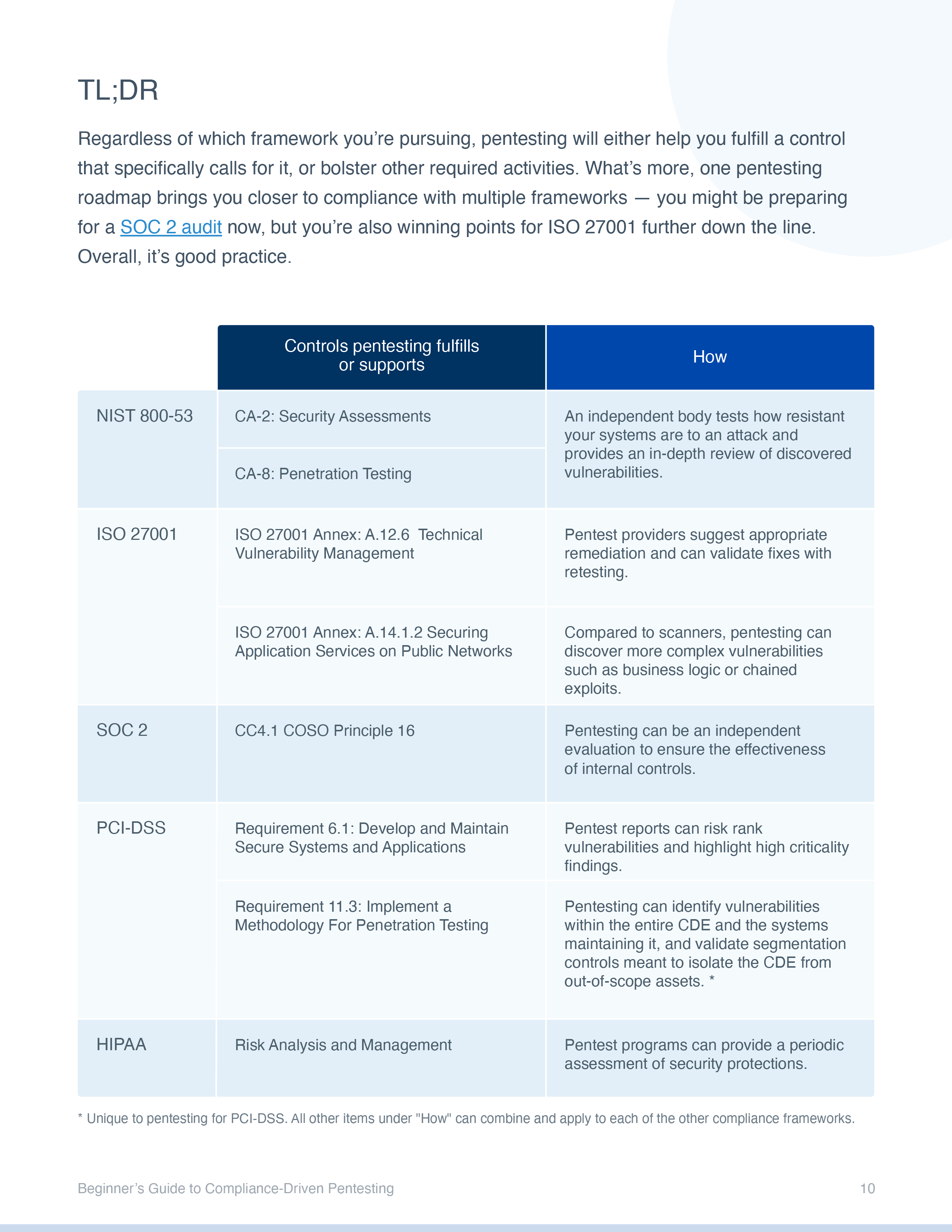
One pentesting roadmap has the potential to win you points for multiple frameworks.
While PCI-DSS has very specific requirements on how you scope and execute your pentests, consistent and regular pentesting can strengthen your security programs and bring you closer to multiple key certifications.
There are multiple well regarded methodologies you can refer to when setting up your first pentest.
For networks, you can rely on the Open Source Security Testing Methodology Manual (OSSTMM) and Center for Internet Security (CIS) Controls, while the OWASP Top 10 application security risks are a great place to start for your applications and APIs. A reputable pentest provider will follow these guidelines.
A formalized pentest program can help you consistently meet compliance obligations, and gradually mature your security programs.
A series of regular pentests can inform secure development, provide performance data and guide strategic decisions.
Annual pentesting may be enough for compliance, but it’s unlikely to be the best option.
Your business should set a pentest cadence based on security needs, customer expectations, and business objectives.