Key Takeaways:
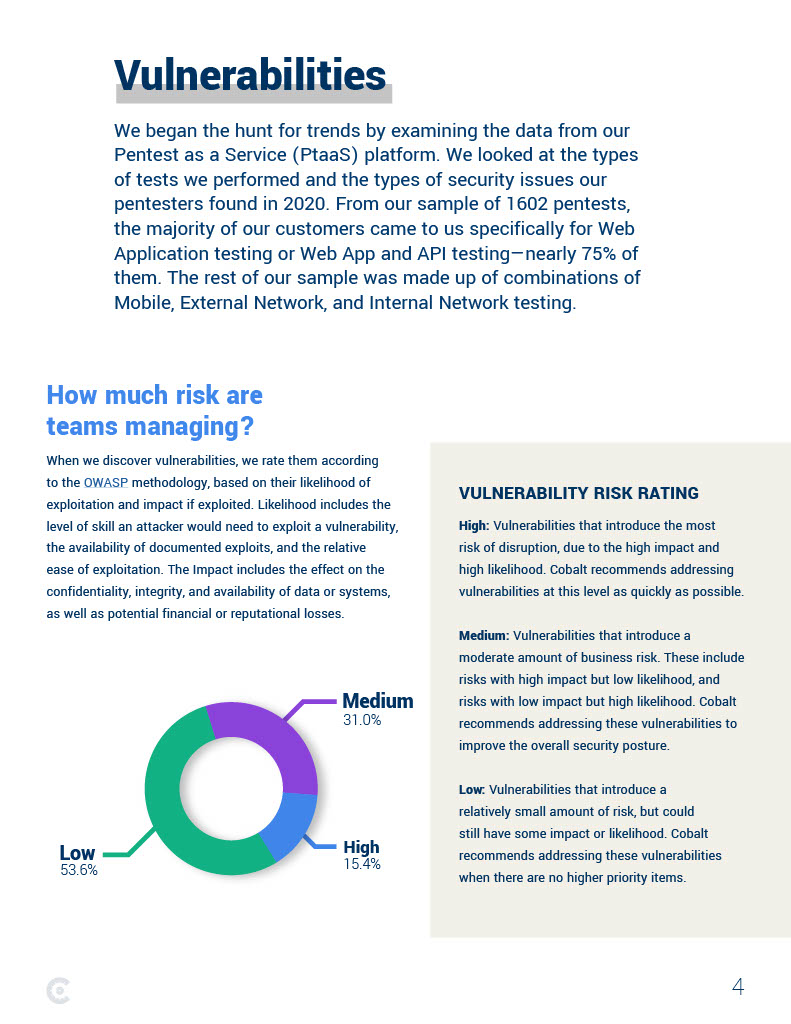
How much risk are teams managing?
.png?width=399&height=221&name=2021-state-of-pentesting-risk-management-graphic%20(1).png)
Most common types of findings
- Broken Access Control: Insecure Direct Object References (IDOR)
- Cross-Site Scripting: Stored
- Components with Known Vulnerabilities: Outdated Software
- Broken Access Control: Username/Email Enumeration
- Cross-Site Scripting: Reflected

|
6 out of 10 see remediated issues
reemerge at a later date |
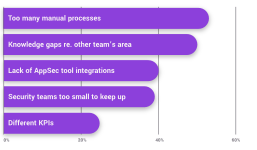
What reduces the effectiveness of prevention & remediation?
What are the biggest challenges when implementing DevSecOps?
|
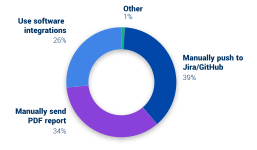
How does security share pentest findings with the remediation team?
|